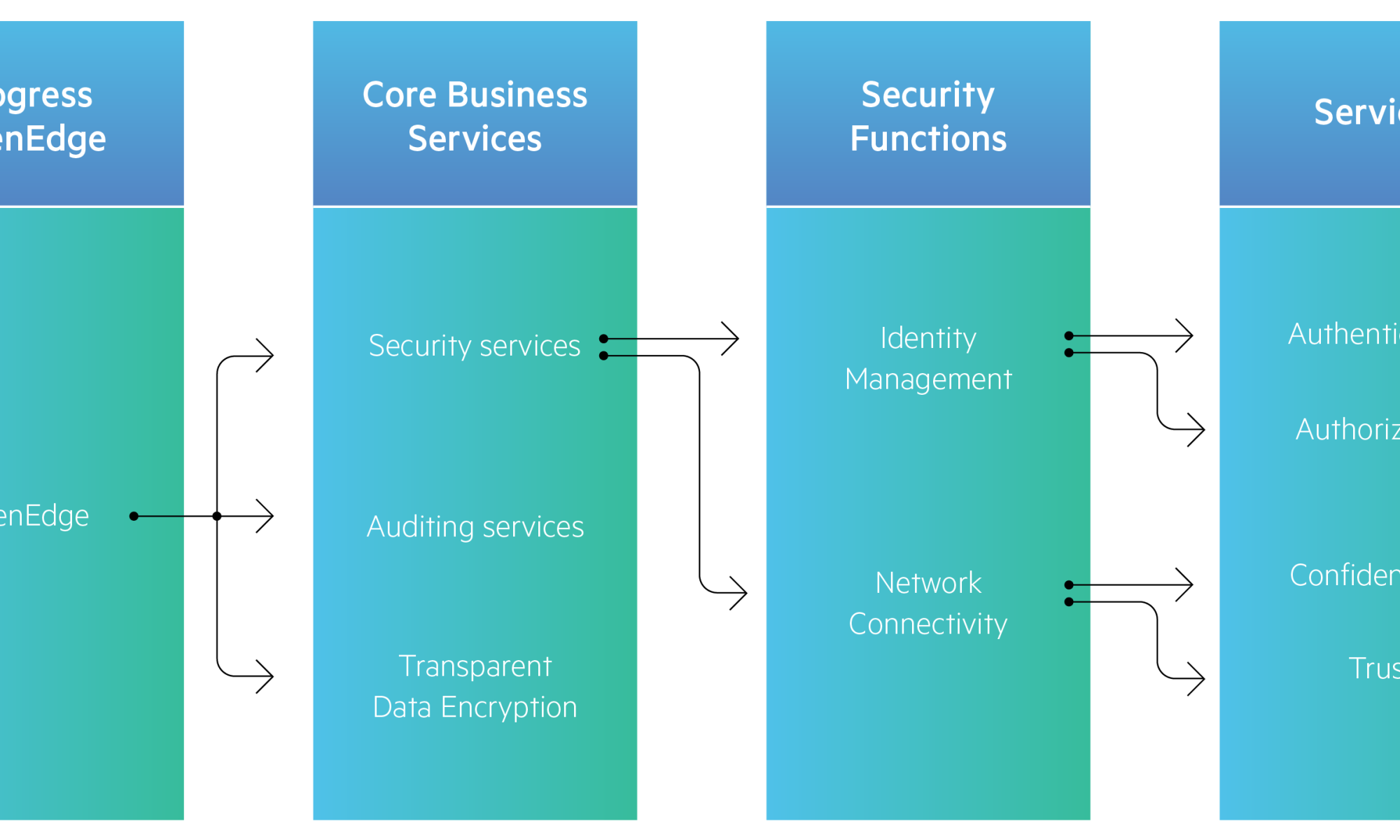
You want to secure your business applications, but the attacks come from all sides. Where to start? Your application data, both at rest and in motion, is the hacker’s prime target. That’s why your infrastructure should use authentication, authorization, auditing and data security to keep content secure at runtime.

Telling stories about music, tech, beauty & lifestyle.